Recently while working in my lab, I was trying to setup VRF Lite in NSX-T 3.0, I came across a bug which was preventing me to turn-on BGP on VRF gateway via UI. This bug has affected 3.0.1 and 3.0.1.1 versions of NSX-T. The error which I was getting when trying to enable BGP was:
“Only ECMP, enabled, BGP Aggregate to be configured for VRF BGP Config”
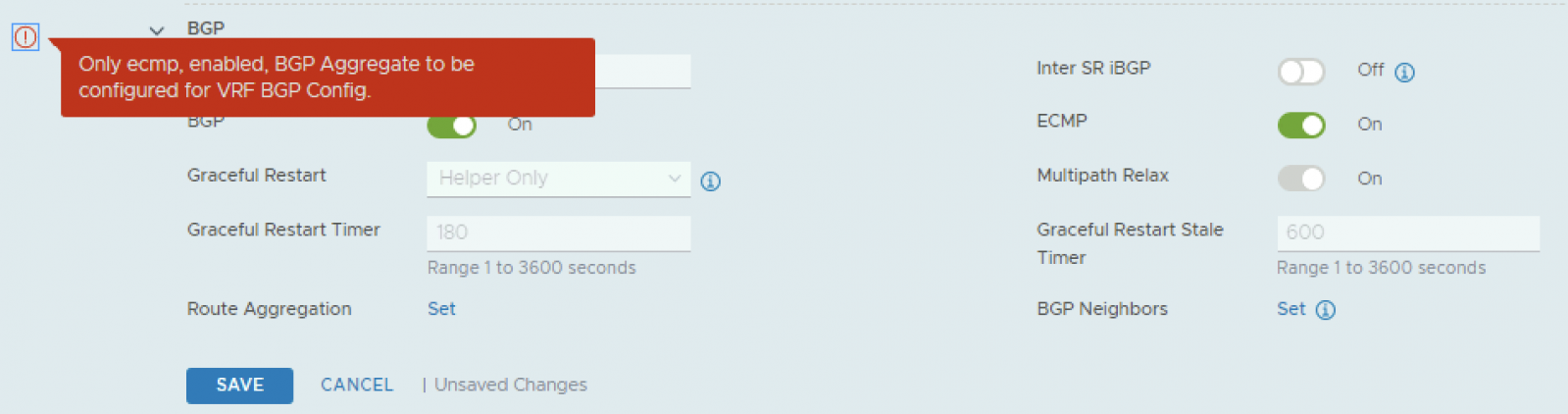
After researching for a bit, I figured out that currently there is no resolution of this issue and API is the only method via which BGP can be turned on on VRF gateway. Below are the steps of doing so.
Step 1: Find Tier-0 ID of the VRF Gateway
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
Method: GET URL: https://{{nsx_mgr}}/policy/api/v1/infra/tier-0s Auth: Basic, admin/<NSX-T Password> Sample Output: { "resource_type":"Tier0", "id":"TenantB-VRF", "display_name":"Tenant-B-VRF", "path":"/infra/tier-0s/TenantB-VRF", "relative_path":"TenantB-VRF", "parent_path":"/infra", "unique_id":"7ff1bbfc-b5cb-433d-8c6c-50df19d320ee", "marked_for_delete":false, "overridden":false, "_create_user":"admin", "_create_time":1600262677856, "_last_modified_user":"admin", "_last_modified_time":1600263587599, "_system_owned":false, "_protection":"NOT_PROTECTED", "_revision":1 } |
From above output, we can see VRF id is “TenantB-VRF”
Step 2: Find Locale Service ID of VRF Gateway
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
Method: GET URL: https://{{nsx_mgr}}/policy/api/v1/infra/tier-0s/<VRF-ID>/locale-services Auth: Basic, admin/<NSX-T Password> Sample Output: { "edge_cluster_path":"/infra/sites/default/enforcement-points/default/edge-clusters/2f525fc1-1e12-4ac5-9c50-f22d6d1588c1", "resource_type":"LocaleServices", "id":"default", "display_name":"default", "path":"/infra/tier-0s/TenantB-VRF/locale-services/default", "relative_path":"default", "parent_path":"/infra/tier-0s/TenantB-VRF", "unique_id":"b6cdc60d-2943-4168-bae2-a9065c64f37f", "marked_for_delete":false, "overridden":false, "_create_user":"admin", "_create_time":1600262677964, "_last_modified_user":"admin", "_last_modified_time":1600262677966, "_system_owned":false, "_protection":"NOT_PROTECTED", "_revision":0 } |
From above output, we can see Locale Service ID is “default”
Step 3: Prepare json payload for BGP enablement
To find out syntax of json payload that we need to enable BGP on VRF, we can first grab the existing state of BGP
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
Method: GET URL: https://{{nsx_mgr}}/policy/api/v1/infra/tier-0s/<VRF-ID>/locale-services/<locale-service-id>/bgp Auth: Basic, admin/<NSX-T Password> Sample Output: { "enabled":false, "ecmp":true, "resource_type":"BgpRoutingConfig", "id":"bgp", "display_name":"bgp", "path":"/infra/tier-0s/TenantB-VRF/locale-services/default/bgp", "relative_path":"bgp", "parent_path":"/infra/tier-0s/TenantB-VRF/locale-services/default", "unique_id":"4f39141f-ee01-48a9-af68-e8e395bca1b4", "marked_for_delete":false, "overridden":false, "_create_user":"admin", "_create_time":1600262677983, "_last_modified_user":"admin", "_last_modified_time":1600262677985, "_system_owned":false, "_protection":"NOT_PROTECTED", "_revision":0 } |
Step 4: Enable BGP on VRF
To enable BGP, we need to take complete API output from step-3 and change “enabled”: false to “enabled”: true and pass this output as payload of PATCH call.… Read More