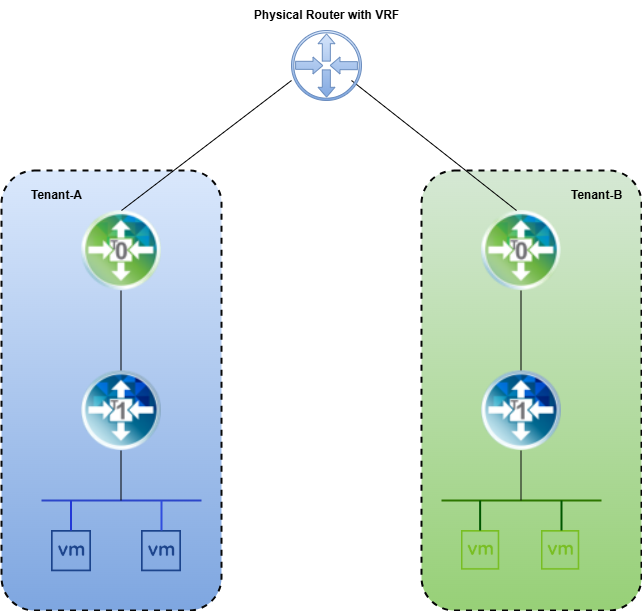
Welcome to part 5 of the NSX VRF series. In part 4, I discussed Inter-VRF routing that enables communication between VRF gateways in NSX by exchanging the routes that are not BGP, e.g., connected, NAT, and static routes, etc. In this post, I will discuss how route exchange can be facilitated over BGP.
If you are not following along, I encourage you to read the earlier parts of this series from the links below:
1: NSX VRF Gateway – Architecture & Configuration
2: VRF Config Validation & Traffic Flows
Introduction
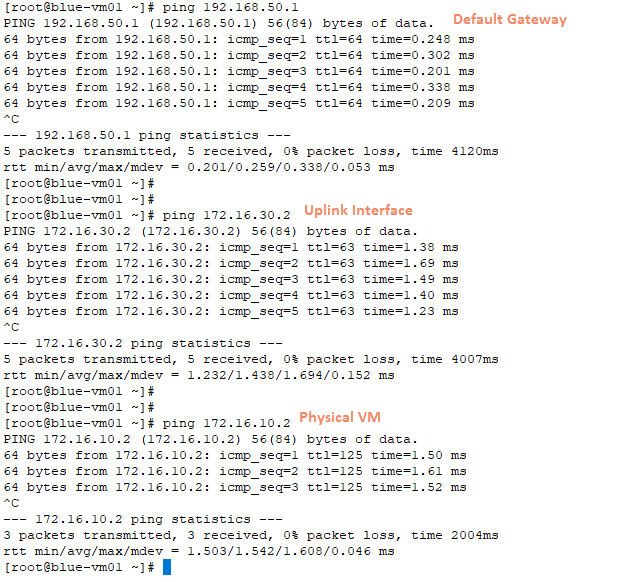
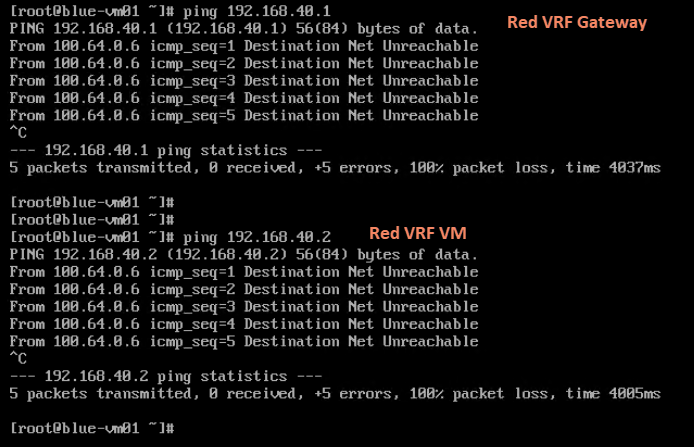
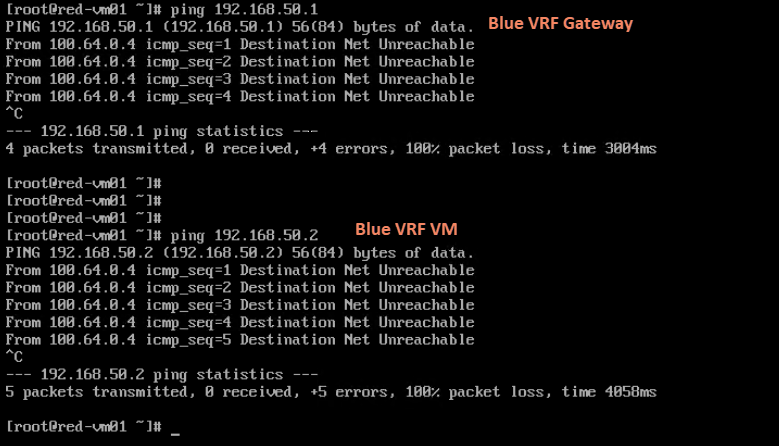
Inter-VRF BGP route leaking allows routes learned in one VRF to be advertised to another VRF over BGP to enable communication between the isolated VRFs. It’s achieved through configuring BGP on Tier-0 VRF gateways and utilizing route maps and community lists to control the route leaking process.
BGP route leaking supports leaking both IPv4 & IPv6 address families.… Read More