VMware Cloud Director 10.2 release introduced key features in the networking and security areas and bridged the gap between VCD and NSX-T integration. In this release of VCD, the following NSX-T enhancements are added:
- VRF Lite support
- Distributed Firewall
- Cross-VDC networking
- NSX Advanced Load Balancer (Avi) integration
These improvements will help partners expand their network and security services with VMware Cloud Director and NSX-T.
In this post, I will be talking about tenant networking using NSX-T VRF Lite.
One of the key components in VCD networking is External Network which provides uplink connectivity to tenant virtual machines to allow them to talk to the outside world (Internet, VPN etc). External networks can be either
- Shared: Allowing multiple tenant edge gateways to use the same external network.
- Dedicated: One-to-one relationship between the external network and the NSX-T edge gateway, and no other edge gateways can connect to the external network.
Dedicating an external network to an edge gateway provides tenants with additional edge gateway services, such as Route Advertisement management and BGP configuration.
A Tier-0 gateway can be dedicated to an external network to offer a fully routed network topology, but it has certain limitations.
In environments where a dedicated external network is needed, you need a tier-0 gateway per tenant. Since we can only have one tier-0 per edge node, we need to deploy additional edge nodes per tenant to have external networks dedicated to that tenant. For edges in VM form factor, this is not an issue, but for bare metal edges, this is not a viable solution and imposes scalability issues.
VRF Lite support was added in NSX-T 3.0 and with VCD 10.2, it’s possible to use NSX-T VRF gateway as an external network. A single tier-0 gateway can support up to 100 VRFs, which improves scalability a lot. VRF Lite is designed to provide data plane isolation through Virtual Routing Forwarding (VRF) in tier-0 gateway.
Tenant consumes VRF Gateway in the same way Tier-0 gateway was consumed in past. VRF gateway creation in NSX-T and importing it as an external network in VCD is still Cloud Provider responsibility. The external network can either connect to Tier-0 or VRF gateway but not to both at once.
Now since we have some background about VRF-Lite, it’s time to jump into the lab and configure the same.
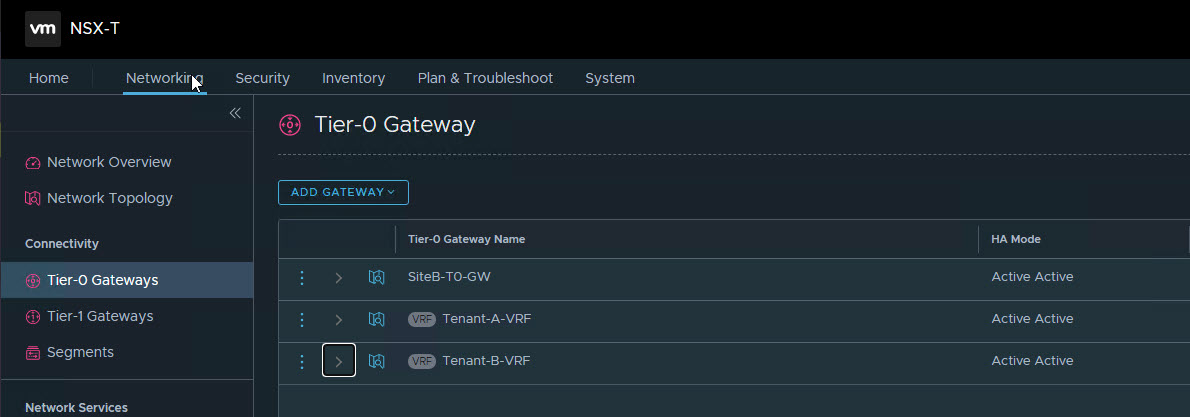
1: Create VRF Gateways in NSX-T: Provider admin creates VRF gateways for the tenants in NSX-T. If you are new to VRF-Lite, then I would recommend reading this post which I wrote sometime back on VRF implementation.
I have created 2 VRF’s in my lab for Tenant A & B. VLANs trunked on VRF for Tenant-A is in the range 10-19 and for Tenant-B in the range 20-29.
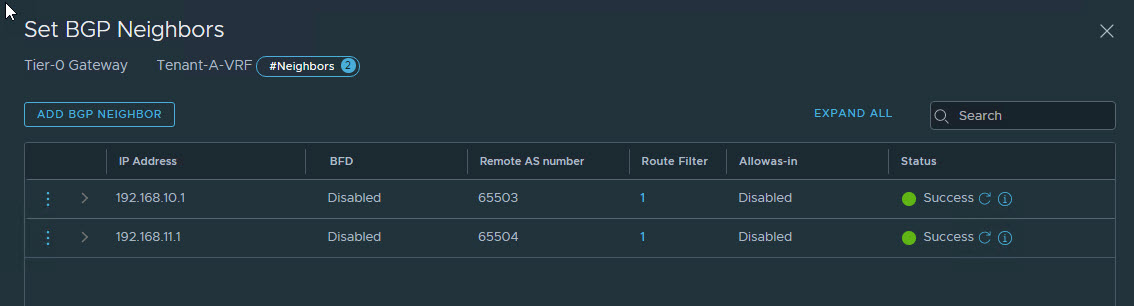
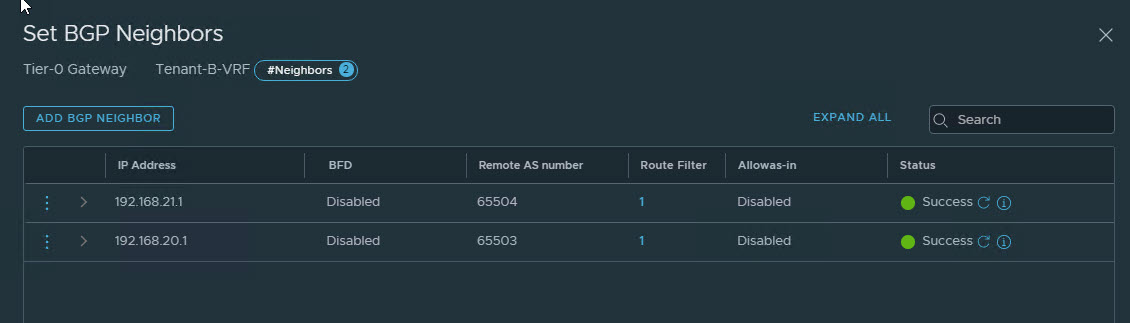
Both VRF gateways are BGP peering with upstream routers.
Before configuring VCD, I assume the following items are already configured:
- Compute vCenter is registered.
- Compute NSX-T manager is registered.
- Geneve backed Network Pool is created.
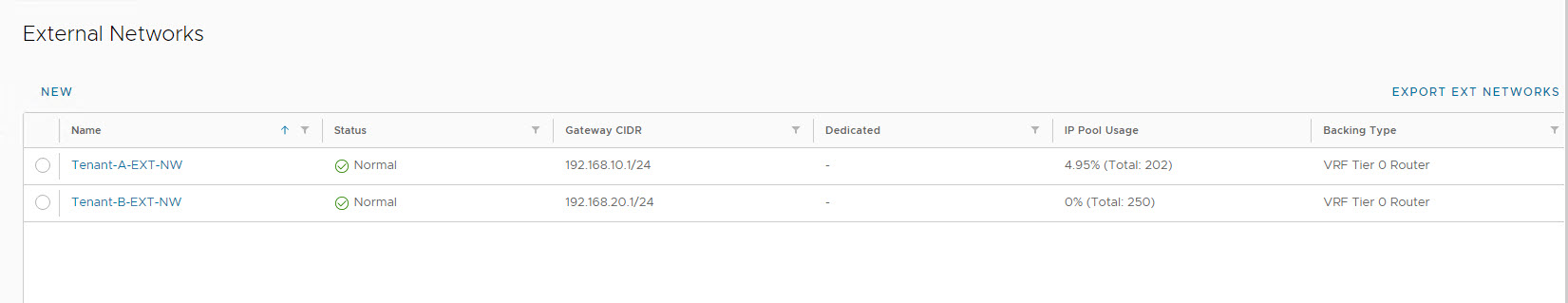
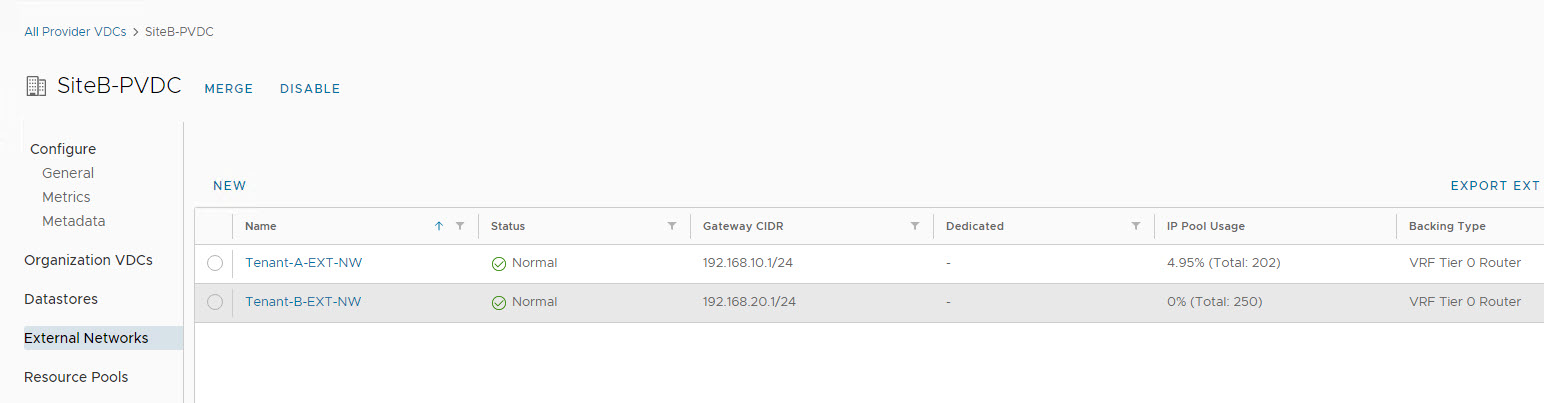
Create an External Network
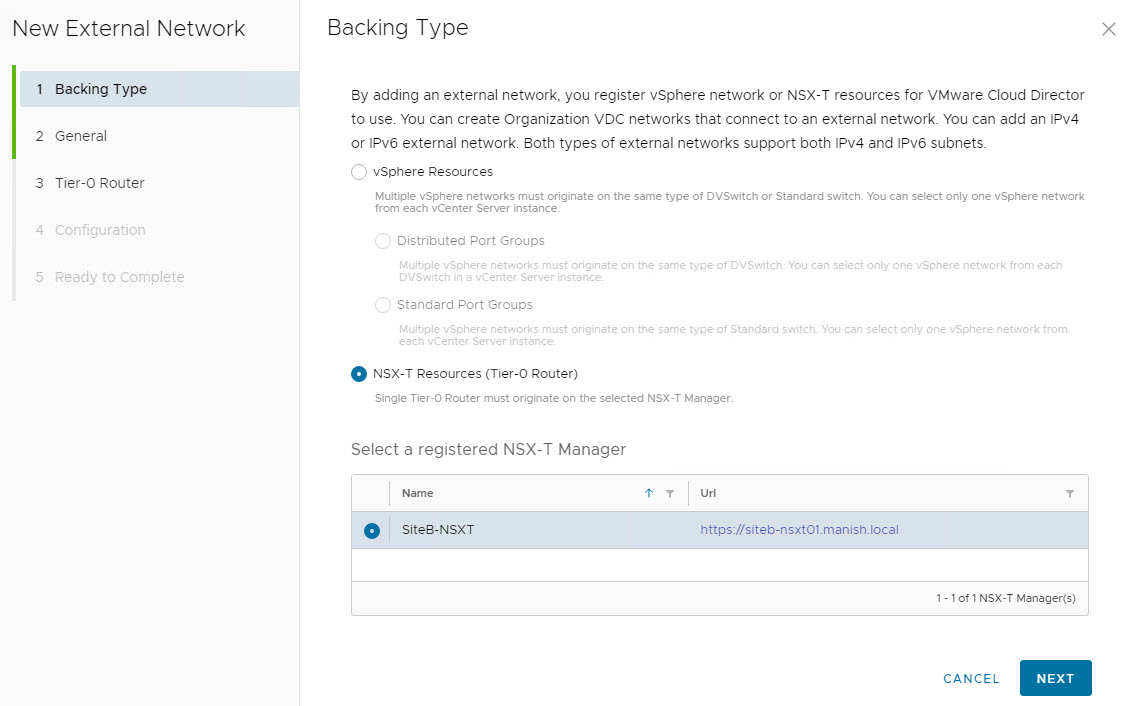
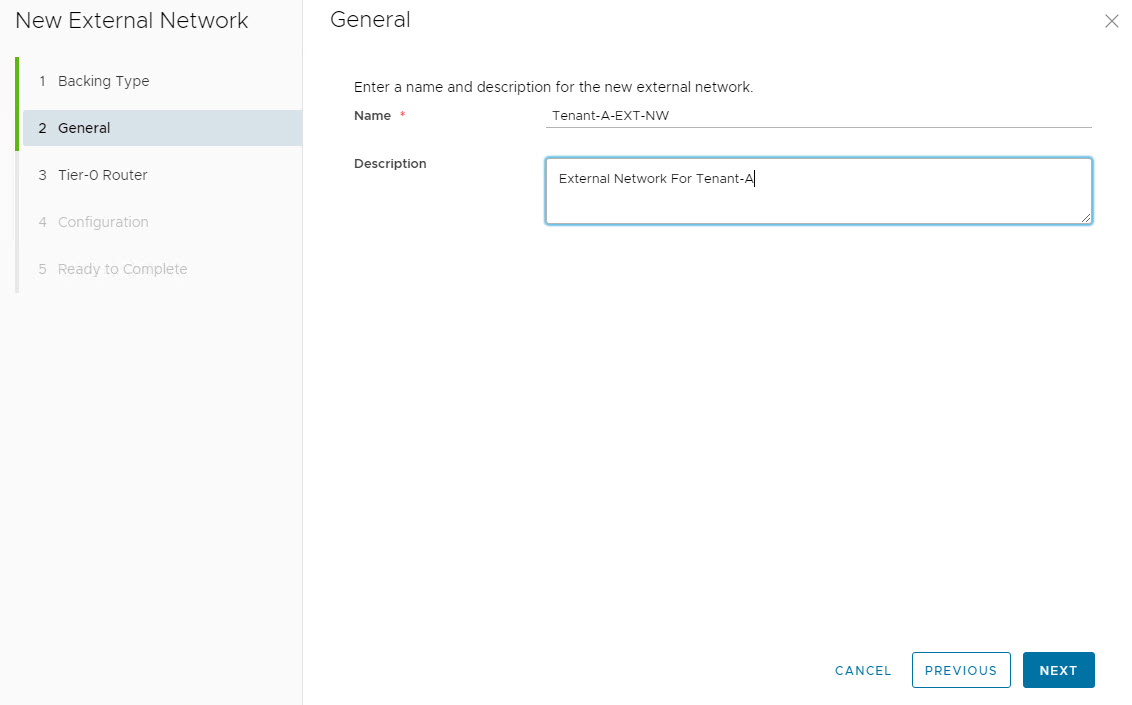
To create an external network, login to VCD, and navigate to Cloud Resources > External Networks and click on New.
Select backing type as NSX-T Resources and choose the registered NSX-T manager.
Provide name and description (optional) for the external network.
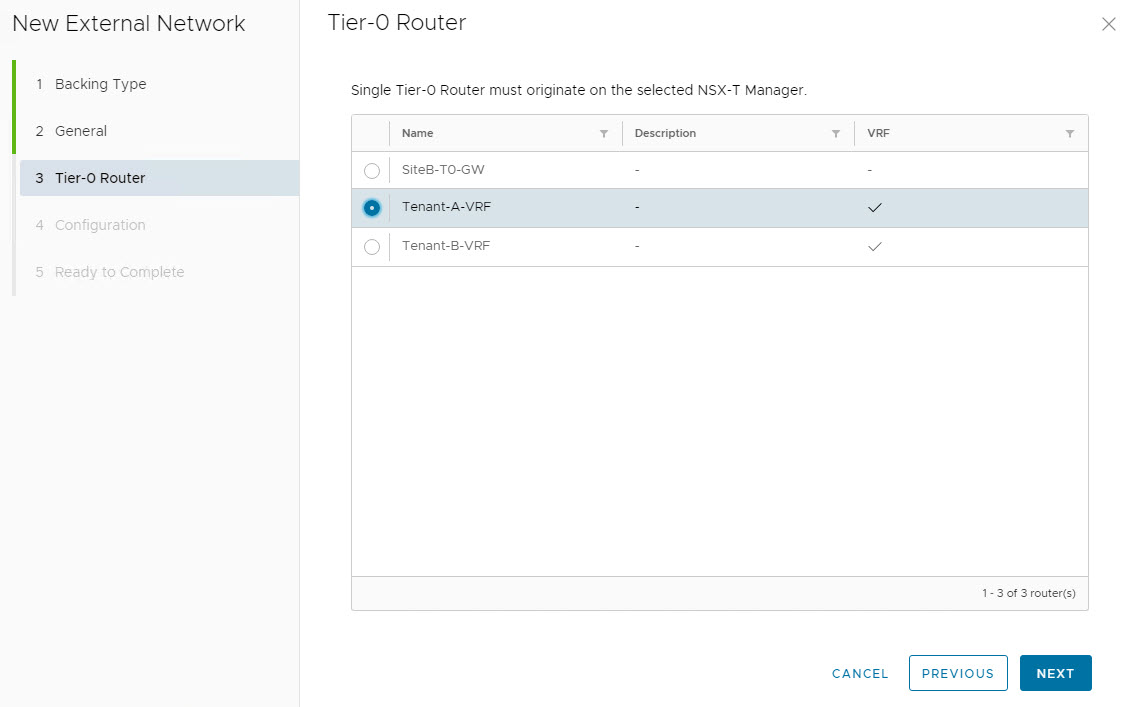
Under Tier-0 Router, select the VRF gateway belonging to Tenant-A.
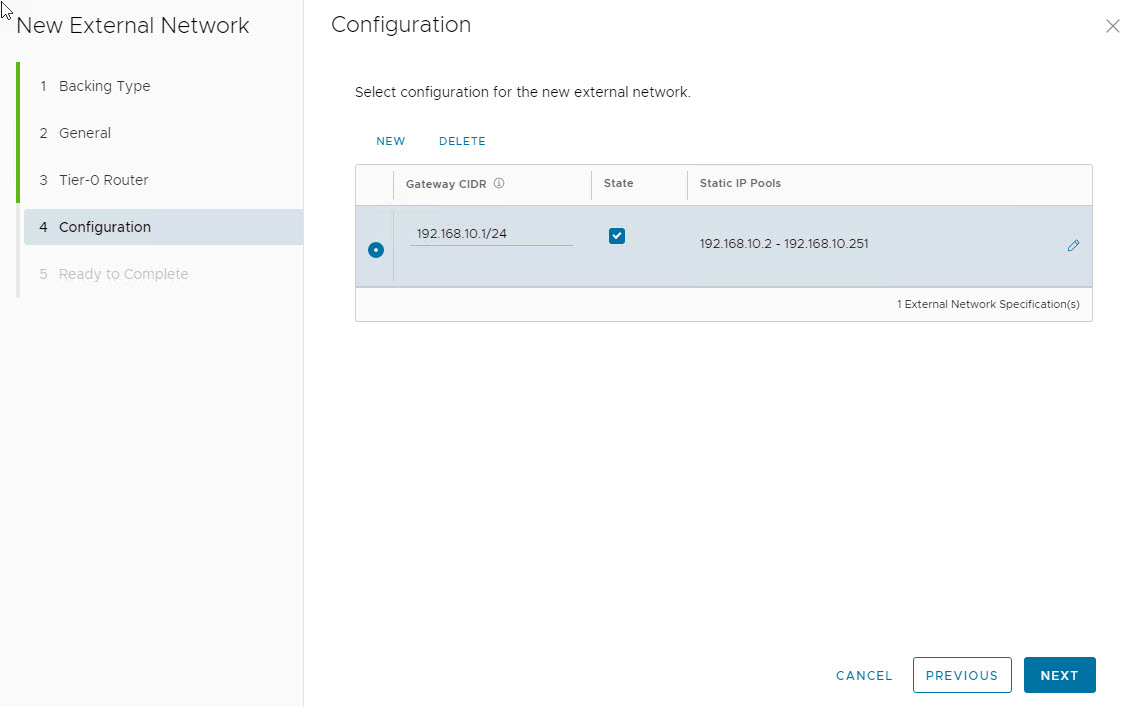
Specify a “gateway” IP address that will be configured on the Tenant-A VRF enabled Tier-0 Gateway.
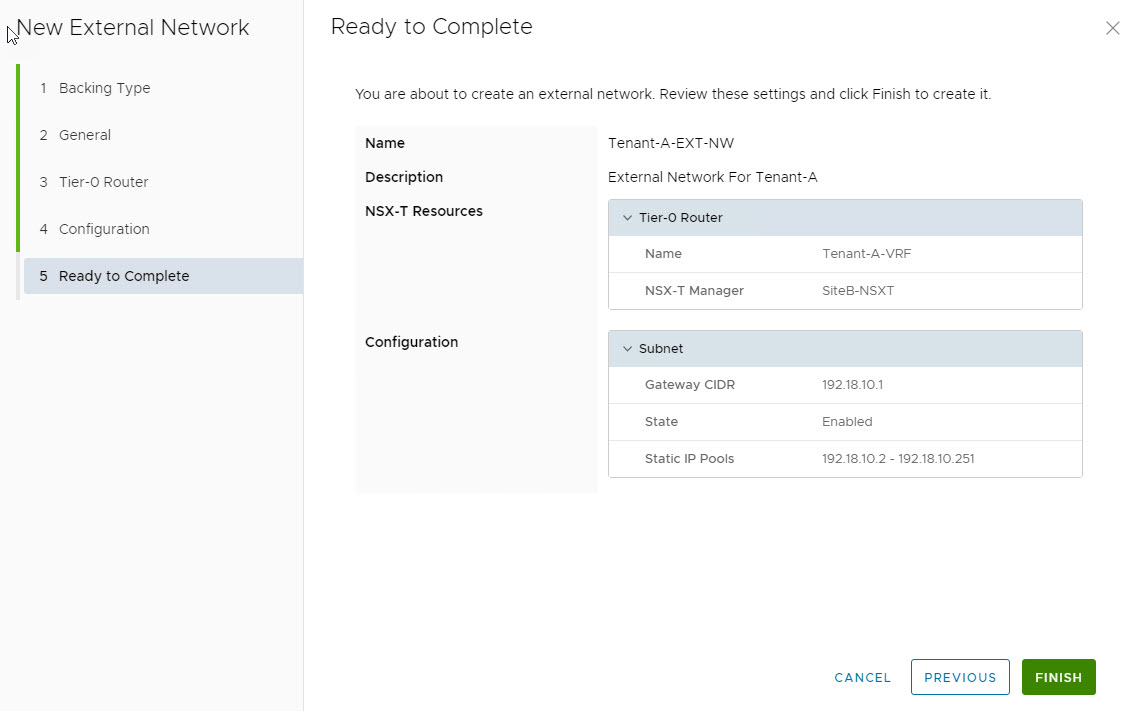
Review your settings and hit finish to complete the External Network creation wizard.
Repeat the process for Tenant-B
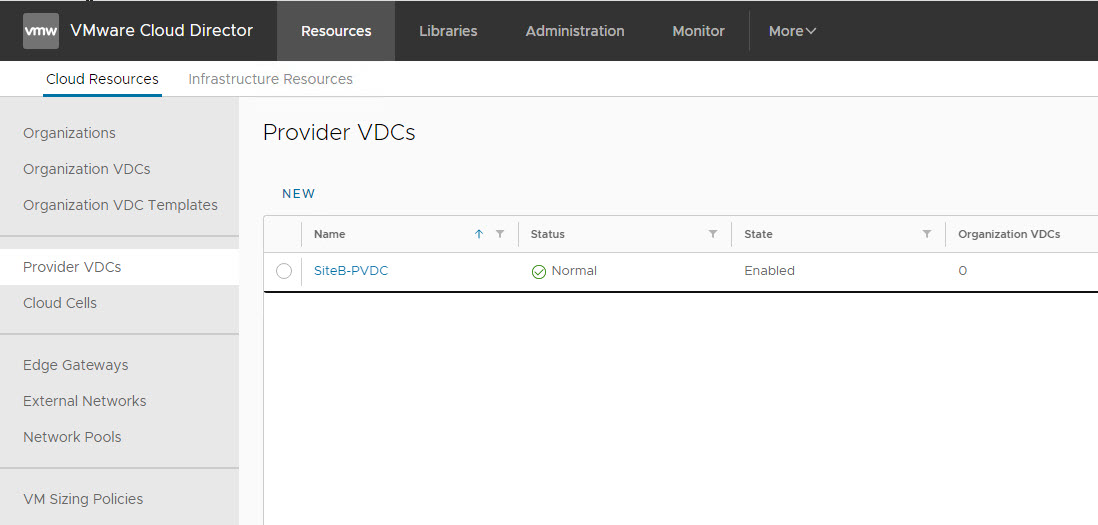
Create Provider VDC
To create a new PVDC, navigate to Cloud Resources > Provider VDCs and click on New.
External Networks created earlier are associated with PVDC during creation.
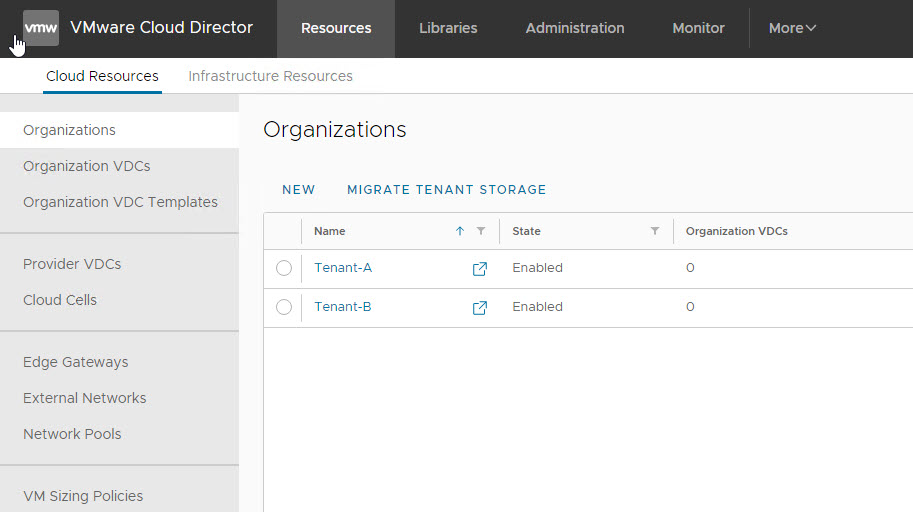
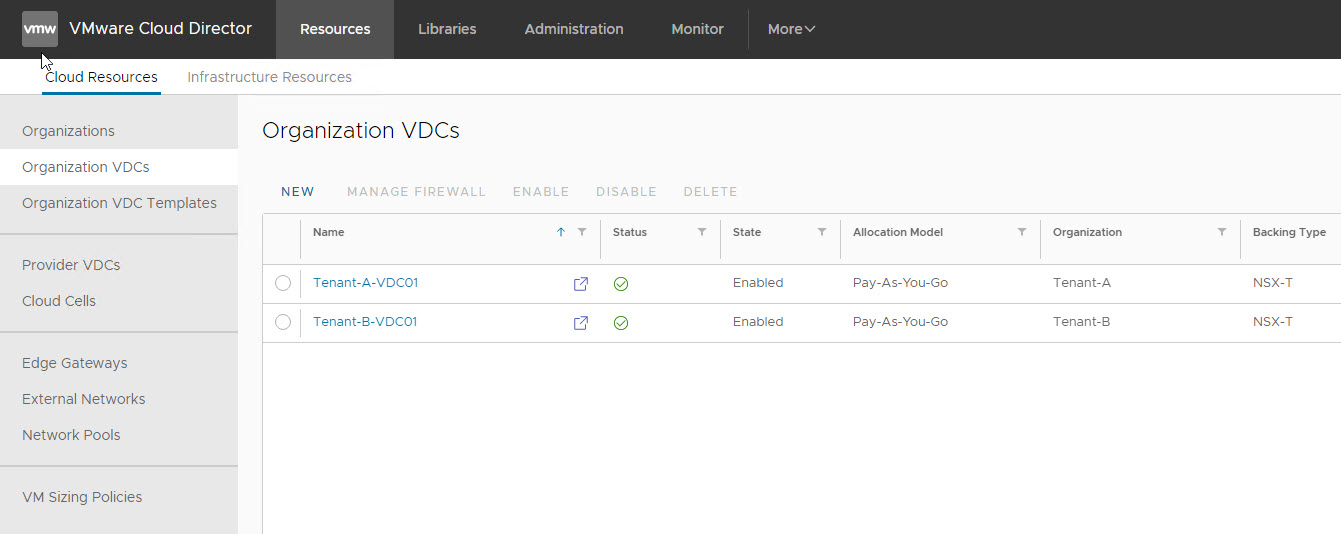
Create an Organization & Organization VDCs
I have 2 Org’s created for the two tenants.
Each org has one VDC created.
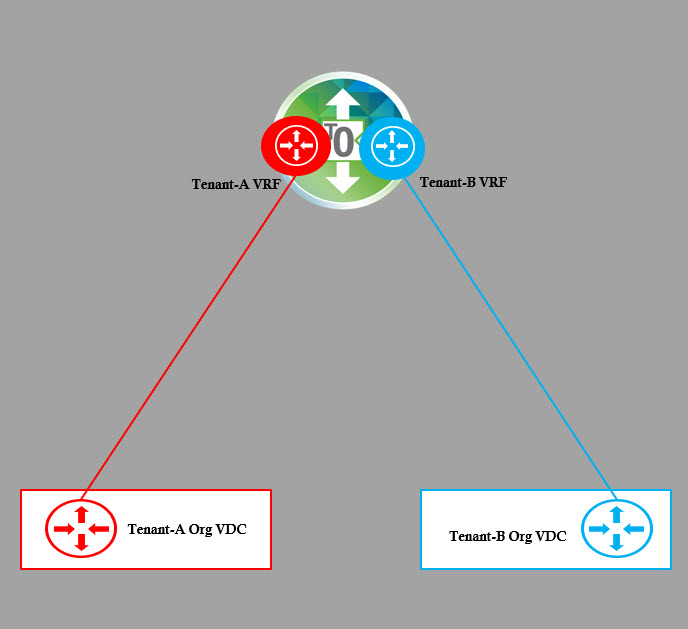
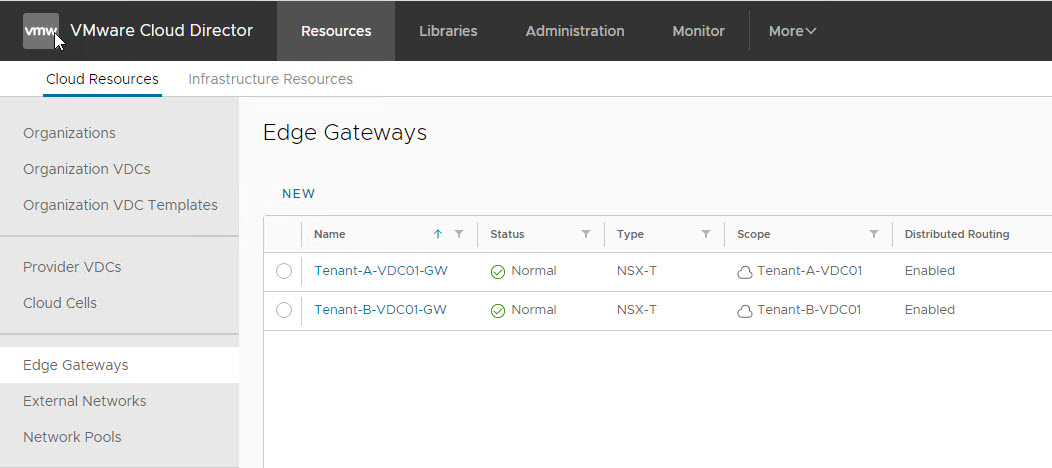
Create Edge Gateways Per Tenant
Edge gateways created for tenants from VCD UI is created as Tier-1 gateway in NSX-T. An Org VDC can have multiple gateways associated with it.
These Edge Gateways will be connected to the VRF enabled Tier-0 Gateways as shown in the below diagram.
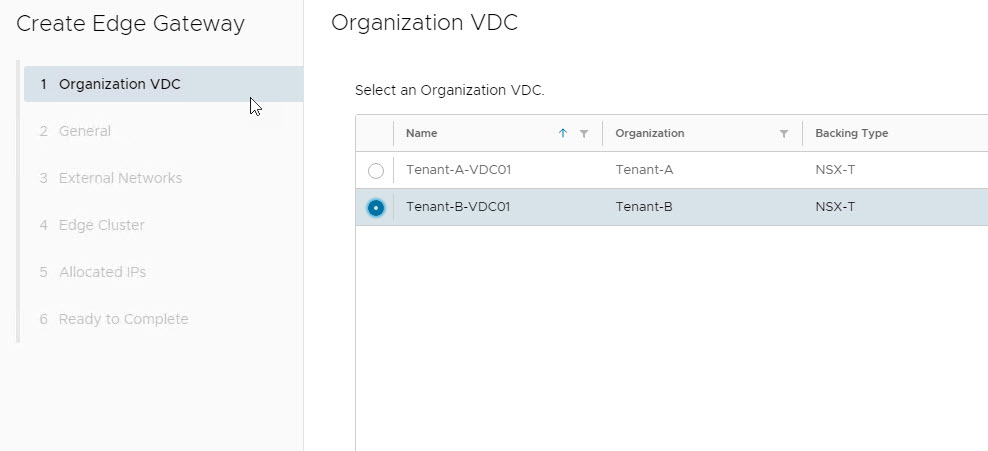
To create an edge gateway for a tenant, navigate to Cloud Resources > Edge Gateways > New.
Select the VDC with which this edge gateway will be associated.
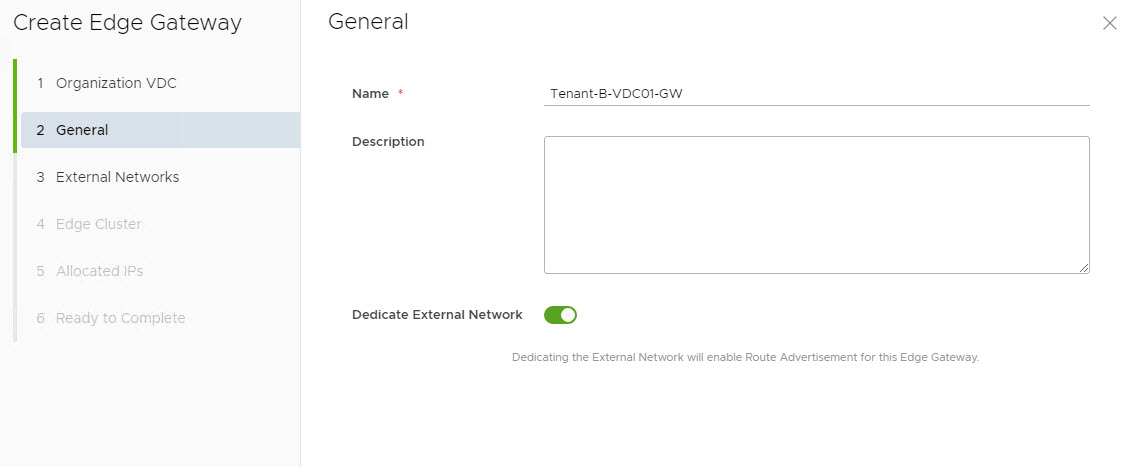
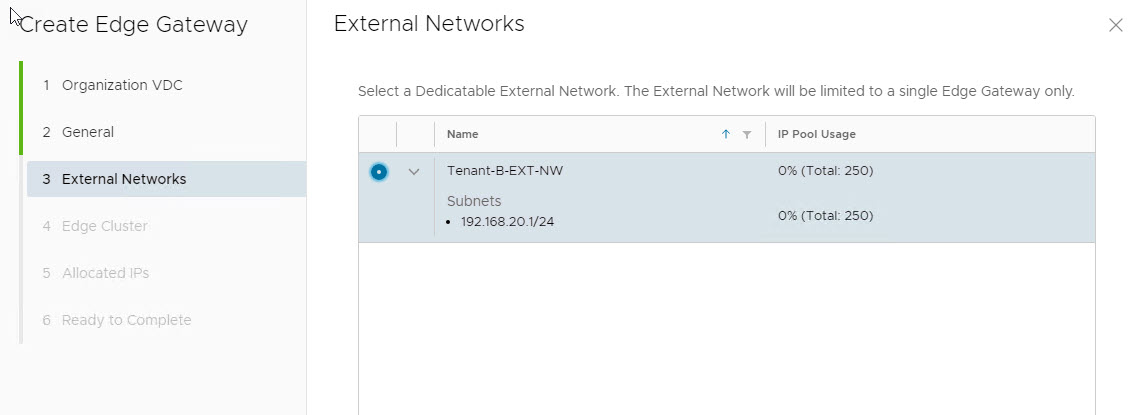
Provide a name for the gateway and toggle the Dedicate External Network button to enable it.
Select the external network that will be associated with the edge gateway.
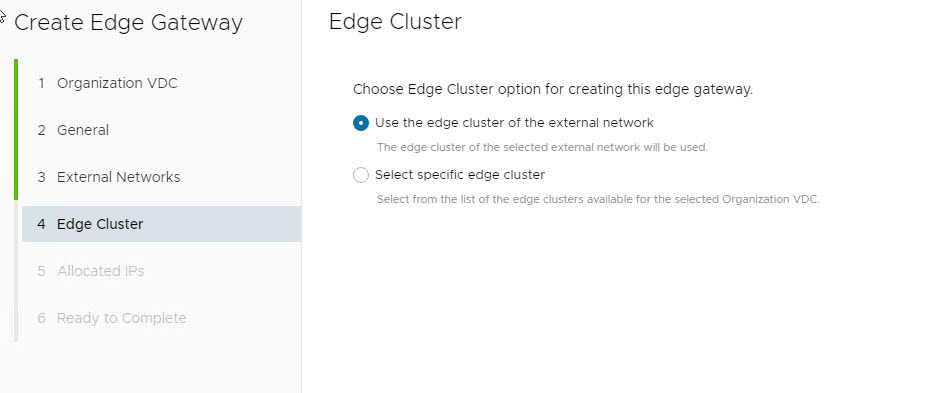
Select specific edge cluster option is used when you have a dedicated Edge Cluster for the Tier-1 Gateways.
Use the edge cluster of the external network means that Tier-0 gateway and its corresponding VRF will all be configured on one Edge Node Cluster.
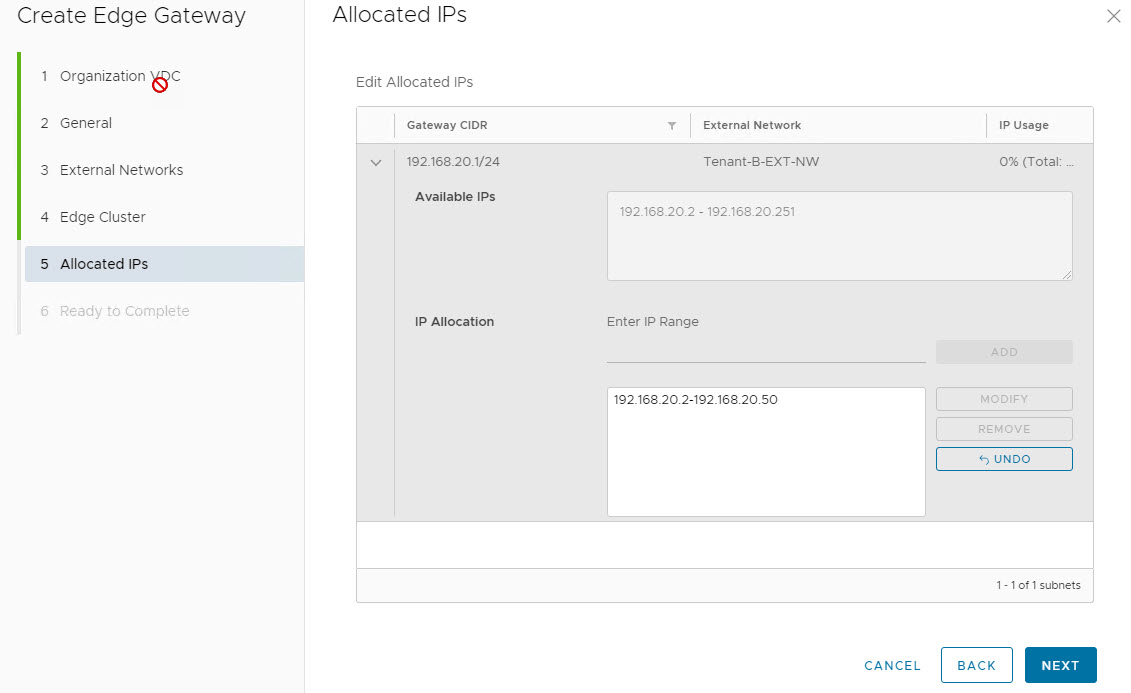
For edge gateway IP Allocation, select a subset of IP from the available IP’s. This IP is used when working with edge gateway NAT rules.
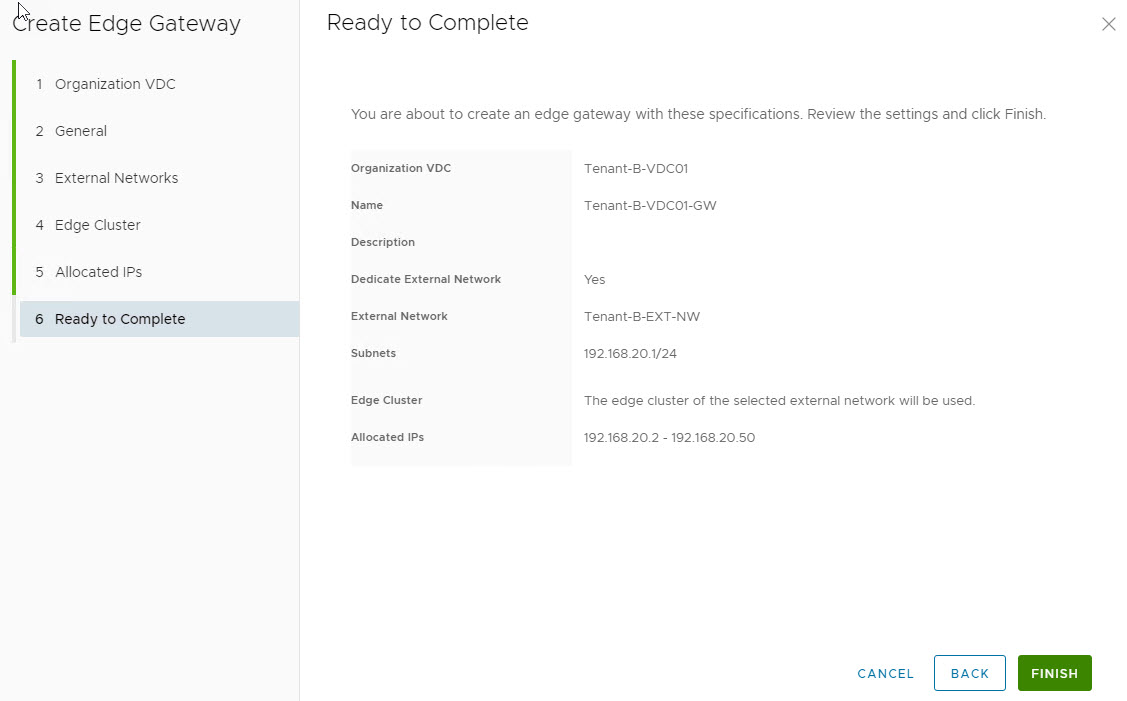
Review the summary and hit finish.
Here are the 2 edge gateways in my lab corresponding to Tenant A & B.
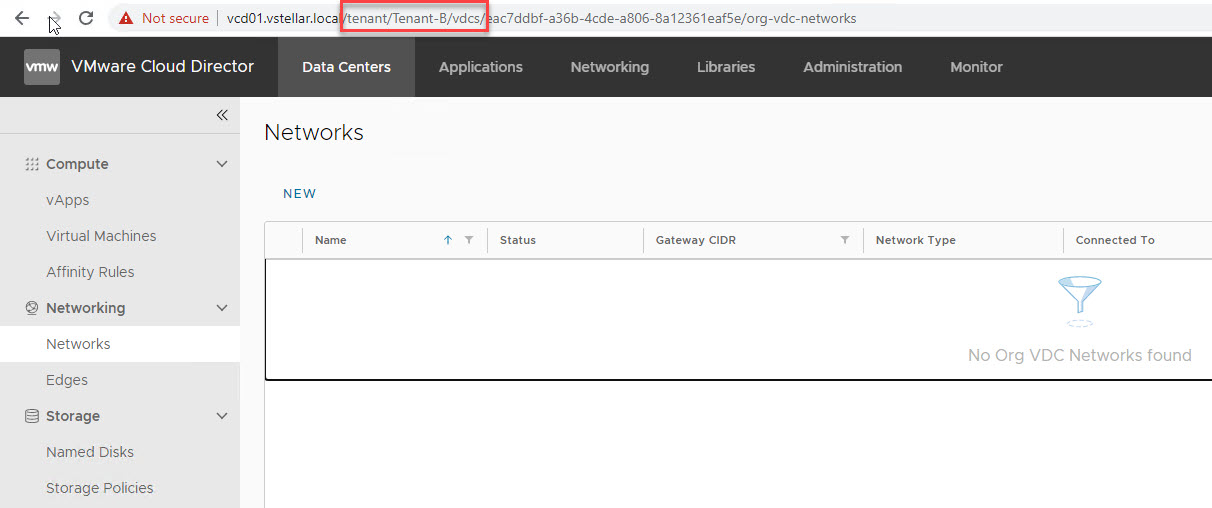
Create an Organization VDC Network
To create Org VDC networks, switch to tenant view and navigate to Data Centers > Networking > Networks, and click on New.
The below slideshow demonstrate the org vdc network creation wizard.
Connectivity Test
Now since tenant networking is in place, it’s time to validate network connectivity.
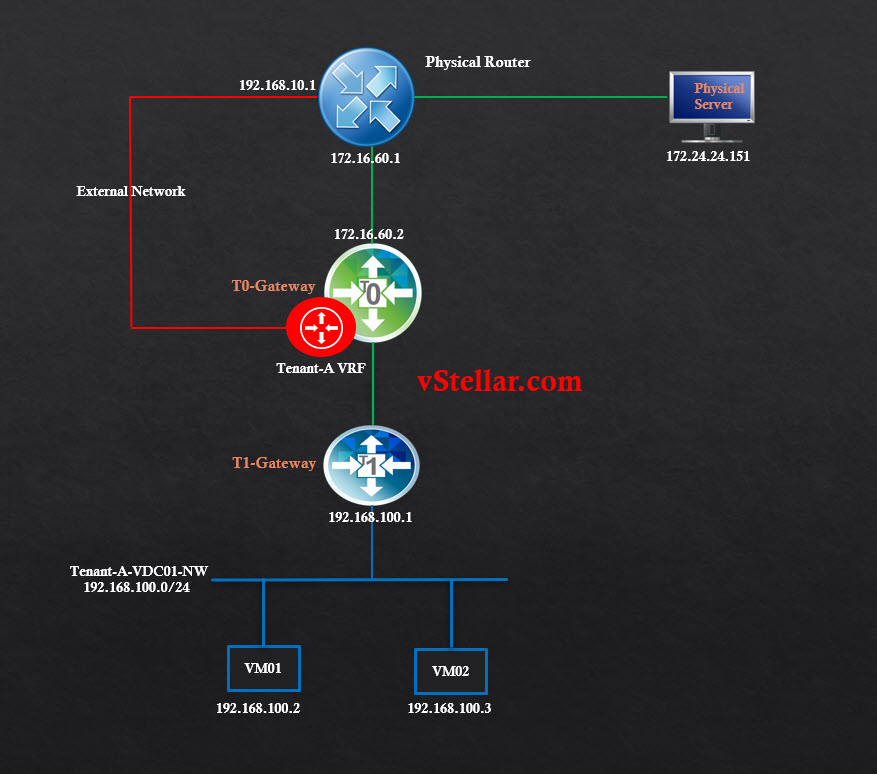
Below is the logical diagram of my lab post tenant network setup.
In order to verify connectivity, I am going to test the reachability of the following IPs:
- 192.168.100.1 (VM-01 gateway)
- 192.168.10.50 (One of the IP on VRF gateway)
- 172.16.60.1 (T0 gateway IP on physical switch)
- 192.168.10.1 (VRF gateway IP on physical switch)
- 172.24.24.151 (Physical DNS Server)
- google.com to test internet connectivity.
The below slideshow contains ping results of above mentioned IPs.
And that concludes this post.
I hope you enjoyed reading this post. Feel free to share this on social media if it is worth sharing 🙂