In the last post of this series, we deployed a Cassandra node and configured ssl security for Cassandra. In this post, we will be installing RabbitMQ for vCD.
If you are not following along this series, then I recommend reading earlier posts of this series from the links below:
1: vCloud Availability Introduction
2: vCloud Availability Architecture & Components
4: Install Cloud Proxy for vCD
What is RabbitMQ (RMQ)?
RabbitMQ is an open source message-queuing software that helps facilitate message exchange between two or more applications. The exchange of messages is done via a queue, defined by the administrator. An application can publish a message to the queue, which can be retrieved or consumed by a different application.
A message can include any kind of information, for example, it could have information about a process/task that should start on another application may be on another server, or it could be just a simple text message.
The queue-manager software stores the messages until a receiving application connects and takes a message off the queue. The receiving application then suitably processes the message.
Why do we need RMQ for vCloud Director?
When you have a multi-cell vCD deployment in your environment, the vCD cells talk to each other and exchange information. This exchange of information is facilitated via RabbitMQ.
RabbitMQ and vCloud Director utilize the Advanced Message Queuing Protocol (AMQP) to talk to each other.
When a vCloud Director Cell wishes to exchange messages (such as system notifications or any other update) with another vCloud Director cell, it places that message within an AMQP broker (Such as RMQ) in one of the queues defined by the Administrator.
The recipient vCloud Director Cell then retrieves the message from the queue and processes it, and if needed, it can publish a message back to the queue for the source cell from where the message was originated.
In my lab, I deployed a new CentOS 6 VM and verified that its Networking, DNS, and NTP are working fine. Next is to install RabbitMQ.
1: Download and install Erlang RPM.
|
1 2 3 |
[root@mgmt-rmq02 ~]# wget http://www.rabbitmq.com/releases/erlang/erlang-18.3-1.el6.x86_64.rpm [root@mgmt-rmq02 ~]# rpm -ivh erlang-18.3-1.el6.x86_64.rpm |
2: Download and Import RabbitMQ public key
|
1 2 3 |
[root@mgmt-rmq02 ~]# wget https://www.rabbitmq.com/rabbitmq-signing-key-public.asc [root@mgmt-rmq02 ~]# rpm --import rabbitmq-signing-key-public.asc |
3: Download and install RabbitMQ rpm.
|
1 2 3 |
[root@mgmt-rmq02 ~]# wget http://www.rabbitmq.com/releases/rabbitmq-server/v3.6.1/rabbitmq-server-3.6.1-1.noarch.rpm [root@mgmt-rmq02 ~]# rpm -ivh rabbitmq-server-3.6.1-1.noarch.rpm |
4: Configure RabbitMQ by following the steps below:
a: Create testca, server, and client directories in /etc/rabbitmq
|
1 |
[root@mgmt-rmq02 ~]# cd /etc/rabbitmq; mkdir -p testca server client |
b: Create a rabbitmq.config file in the /etc/rabbitmq directory with the below contents
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 |
[root@mgmt-rmq02 rabbitmq]# vim /etc/rabbitmq/rabbitmq.config [{ssl, [{versions, [tlsv1, 'tlsv1.2', 'tlsv1.1']}, {ciphers, ["ECDHE-ECDSA-AES256-GCM-SHA384","ECDHE-RSA-AES256-GCM-SHA384", "ECDHE-ECDSA-AES256-SHA384","ECDHE-RSA-AES256-SHA384", "ECDH-ECDSA-AES256-GCM-SHA384","ECDH-RSA-AES256-GCM-SHA384", "ECDH-ECDSA-AES256-SHA384","ECDH-RSA-AES256-SHA384", "DHE-RSA-AES256-GCM-SHA384","DHE-DSS-AES256-GCM-SHA384", "DHE-RSA-AES256-SHA256","DHE-DSS-AES256-SHA256","AES256-GCM-SHA384", "AES256-SHA256","ECDHE-ECDSA-AES128-GCM-SHA256", "ECDHE-RSA-AES128-GCM-SHA256","ECDHE-ECDSA-AES128-SHA256", "ECDHE-RSA-AES128-SHA256","ECDH-ECDSA-AES128-GCM-SHA256", "ECDH-RSA-AES128-GCM-SHA256","ECDH-ECDSA-AES128-SHA256", "ECDH-RSA-AES128-SHA256","DHE-RSA-AES128-GCM-SHA256", "DHE-DSS-AES128-GCM-SHA256","DHE-RSA-AES128-SHA256","DHE-DSS-AES128-SHA256", "AES128-GCM-SHA256","AES128-SHA256","ECDHE-ECDSA-AES256-SHA", "ECDHE-RSA-AES256-SHA","DHE-RSA-AES256-SHA","DHE-DSS-AES256-SHA", "ECDH-ECDSA-AES256-SHA","ECDH-RSA-AES256-SHA","AES256-SHA", "ECDHE-ECDSA-DES-CBC3-SHA","ECDHE-RSA-DES-CBC3-SHA","EDH-RSA-DES-CBC3-SHA", "EDH-DSS-DES-CBC3-SHA","ECDH-ECDSA-DES-CBC3-SHA","ECDH-RSA-DES-CBC3-SHA", "DES-CBC3-SHA","ECDHE-ECDSA-AES128-SHA","ECDHE-RSA-AES128-SHA", "DHE-RSA-AES128-SHA","DHE-DSS-AES128-SHA","ECDH-ECDSA-AES128-SHA", "ECDH-RSA-AES128-SHA","AES128-SHA","EDH-RSA-DES-CBC-SHA","DES-CBC-SHA"]}]}, {rabbit, [ {tcp_listeners, [5672]}, {ssl_listeners, [5671]}, {ssl_options, [{cacertfile,"/etc/rabbitmq/testca/cacert.pem"}, {certfile,"/etc/rabbitmq/server/cert.pem"}, {keyfile,"/etc/rabbitmq/server/key.pem"}, {versions, [tlsv1, 'tlsv1.2', 'tlsv1.1']}, {verify, verify_peer}, {padding_check, true}, {ciphers, ["ECDHE-ECDSA-AES256-GCM-SHA384","ECDHE-RSA-AES256-GCM-SHA384", "ECDHE-ECDSA-AES256-SHA384","ECDHE-RSA-AES256-SHA384", "ECDH-ECDSA-AES256-GCM-SHA384","ECDH-RSA-AES256-GCM-SHA384", "ECDH-ECDSA-AES256-SHA384","ECDH-RSA-AES256-SHA384", "DHE-RSA-AES256-GCM-SHA384","DHE-DSS-AES256-GCM-SHA384", "DHE-RSA-AES256-SHA256","DHE-DSS-AES256-SHA256","AES256-GCM-SHA384", "AES256-SHA256","ECDHE-ECDSA-AES128-GCM-SHA256", "ECDHE-RSA-AES128-GCM-SHA256","ECDHE-ECDSA-AES128-SHA256", "ECDHE-RSA-AES128-SHA256","ECDH-ECDSA-AES128-GCM-SHA256", "ECDH-RSA-AES128-GCM-SHA256","ECDH-ECDSA-AES128-SHA256", "ECDH-RSA-AES128-SHA256","DHE-RSA-AES128-GCM-SHA256", "DHE-DSS-AES128-GCM-SHA256","DHE-RSA-AES128-SHA256","DHE-DSS-AES128-SHA256", "AES128-GCM-SHA256","AES128-SHA256","ECDHE-ECDSA-AES256-SHA", "ECDHE-RSA-AES256-SHA","DHE-RSA-AES256-SHA","DHE-DSS-AES256-SHA", "ECDH-ECDSA-AES256-SHA","ECDH-RSA-AES256-SHA","AES256-SHA", "ECDHE-ECDSA-DES-CBC3-SHA","ECDHE-RSA-DES-CBC3-SHA","EDH-RSA-DES-CBC3-SHA", "EDH-DSS-DES-CBC3-SHA","ECDH-ECDSA-DES-CBC3-SHA","ECDH-RSA-DES-CBC3-SHA", "DES-CBC3-SHA","ECDHE-ECDSA-AES128-SHA","ECDHE-RSA-AES128-SHA", "DHE-RSA-AES128-SHA","DHE-DSS-AES128-SHA","ECDH-ECDSA-AES128-SHA", "ECDH-RSA-AES128-SHA","AES128-SHA","EDH-RSA-DES-CBC-SHA","DES-CBC-SHA"]}, {fail_if_no_peer_cert,false}]} ]} ]. |
d: Enable and start the RabbitMQ server service.
|
1 2 3 4 5 |
[root@mgmt-rmq02 ~]# chkconfig rabbitmq-server on [root@mgmt-rmq02 rabbitmq]# service rabbitmq-server start Starting rabbitmq-server: SUCCESS rabbitmq-server. |
e: Enable RabbitMQ UI on http://server-name:15672/
|
1 2 3 4 5 6 7 8 9 10 11 |
[root@mgmt-rmq02 rabbitmq]# rabbitmq-plugins enable rabbitmq_management The following plugins have been enabled: mochiweb webmachine rabbitmq_web_dispatch amqp_client rabbitmq_management_agent rabbitmq_management Applying plugin configuration to rabbit@mgmt-rmq02... started 6 plugins. |
f: Create new admin user for RMQ administration
|
1 2 3 4 5 6 7 8 |
[root@mgmt-rmq02 rabbitmq]# rabbitmqctl add_user admin vmware Creating user "admin" ... [root@mgmt-rmq02 rabbitmq]# rabbitmqctl set_permissions -p / admin ".*" ".*" ".*" Setting permissions for user "admin" in vhost "/" ... [root@mgmt-rmq02 rabbitmq]# rabbitmqctl set_user_tags admin administrator Setting tags for user "admin" to [administrator] ... |
RabbitMQ SSL Configuration
1: Install Java on the RMQ node
|
1 |
[root@mgmt-rmq02 ~]# rpm -ivh jdk-8u152-linux-x64.rpm |
2: Create a public and a private key
Note: In the command below, the SAN attribute contains DNS names and IP addresses of all of the RabbitMQ hosts and the load balancer. For a single RMQ node, there will be only one entry.
|
1 |
# keytool -genkeypair -keystore rootca.jks -storepass vmware -keyalg RSA -validity 1826 -keypass vmware -alias rabbitmq -dname "CN=*.alex.local,OU=vStellar.com, O=Alex.Co, L=Bangalore S=Karnataka C=IN" -ext san=dns:mgmt-rmq02.alex.local,ip:192.168.109.35 |
If you have multiple RMQ nodes that are load-balanced via VIP, then modify the above command as shown below
|
1 |
# keytool -genkeypair -keystore rootca.jks -storepass vmware -keyalg RSA -validity 365 -keypass vmware -alias rabbitmq -dname "CN=*.corp-ext.local,OU=Test, O=Corp, L=Palo Alto S=CA C=US" -ext san=dns:test2.corp-ext.local,dns:test3.corp-ext.local,dns:testrabbitmqlb.corp-ext.local,ip:172.31.3.39,ip:172.31.3.40,ip:172.31.3.41 |
3: Import the RabbitMQ key pair to the PKCS12 trust store
|
1 2 3 |
[root@mgmt-rmq02 ~]# keytool -importkeystore -srckeystore rootca.jks -destkeystore foo.p12 -deststoretype pkcs12 -srcstorepass vmware -deststorepass vmware -alias rabbitmq Importing keystore rootca.jks to foo.p12... |
4: Convert the key pair file to PEM format
|
1 2 3 |
[root@mgmt-rmq02 ~]# openssl pkcs12 -in foo.p12 -out foo.pem -passin pass:vmware -passout pass:vmware MAC verified OK |
5: Extract the encrypted private key
|
1 |
[root@mgmt-rmq02 ~]# sed -n '/-----BEGIN ENCRYPTED PRIVATE KEY-----/,/-----END ENCRYPTED PRIVATE KEY-----/p' foo.pem > enc.pem |
6: Decrypt the private key
|
1 2 3 |
[root@mgmt-rmq02 ~]# openssl rsa -in enc.pem -out unenc.pem -passin pass:vmware writing RSA key |
7: Extract the certificate
|
1 |
[root@mgmt-rmq02 ~]# sed -n '/-----BEGIN CERTIFICATE-----/,/-----END CERTIFICATE-----/p' foo.pem > cert.pem |
8: Install the self-signed certificates by copying them to the newly created directories.
|
1 2 3 4 5 6 7 8 9 |
[root@mgmt-rmq02 ~]# cp cert.pem /etc/rabbitmq/testca/cacert.pem [root@mgmt-rmq02 ~]# cp cert.pem /etc/rabbitmq/server/cert.pem [root@mgmt-rmq02 ~]# cp cert.pem /etc/rabbitmq/client/cert.pem [root@mgmt-rmq02 ~]# cp unenc.pem /etc/rabbitmq/server/key.pem [root@mgmt-rmq02 ~]# cp unenc.pem /etc/rabbitmq/client/key.pem |
9: Change the ownership of the newly created directories
|
1 2 3 4 5 |
[root@mgmt-rmq02 ~]# chown -R rabbitmq: /etc/rabbitmq/testca [root@mgmt-rmq02 ~]# chown -R rabbitmq: /etc/rabbitmq/server [root@mgmt-rmq02 ~]# chown -R rabbitmq: /etc/rabbitmq/client |
10: Restart RMQ service
|
1 2 3 |
[root@mgmt-rmq02 ~]# service rabbitmq-server restart Restarting rabbitmq-server: SUCCESS rabbitmq-server. |
Configure a RabbitMQ Cluster
In my lab, I am not setting up a RabbitMQ cluster. But if you want to do so, then the instructions are documented here
RMQ-vCD Integration
Connect to the VCAV appliance via SSH and run the following commands to integrate vCD with RMQ.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
root@mgmt-vcav [ ~ ]# export AMQP_ADDRESS=mgmt-rmq02.alex.local root@mgmt-vcav [ ~ ]# export VCD_USER=admin root@mgmt-vcav [ ~ ]# export VCD_ADDRESS=192.168.109.30 root@mgmt-vcav [ ~ ]# vcav trust add --address=$AMQP_ADDRESS --port=5671 --accept-all WARNING - Trusting 3D:DF:04:D7:5E:0C:0C:DA:2A:39:68:51:B7:4C:BB:BA:54:FF:A8:32 for mgmt-rmq02.alex.local:5671 OK root@mgmt-vcav [ ~ ]# vcav vcd configure-amqp --vcd-address=$VCD_ADDRESS --vcd-user=$VCD_USER --vcd-password-file=~/.ssh/.vcd --amqp-address=$AMQP_ADDRESS --amqp-port=5671 --amqp-user=admin --amqp-password-file=~/.ssh/.amqp --amqp-vhost=/ --amqp-exchange=systemExchange OK |
Log in to vCD to validate the RMQ configuration under System > Administration > Extensibility
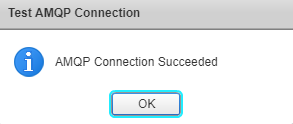
Click on Test AMQP Connection to verify vCD can talk to RMQ.
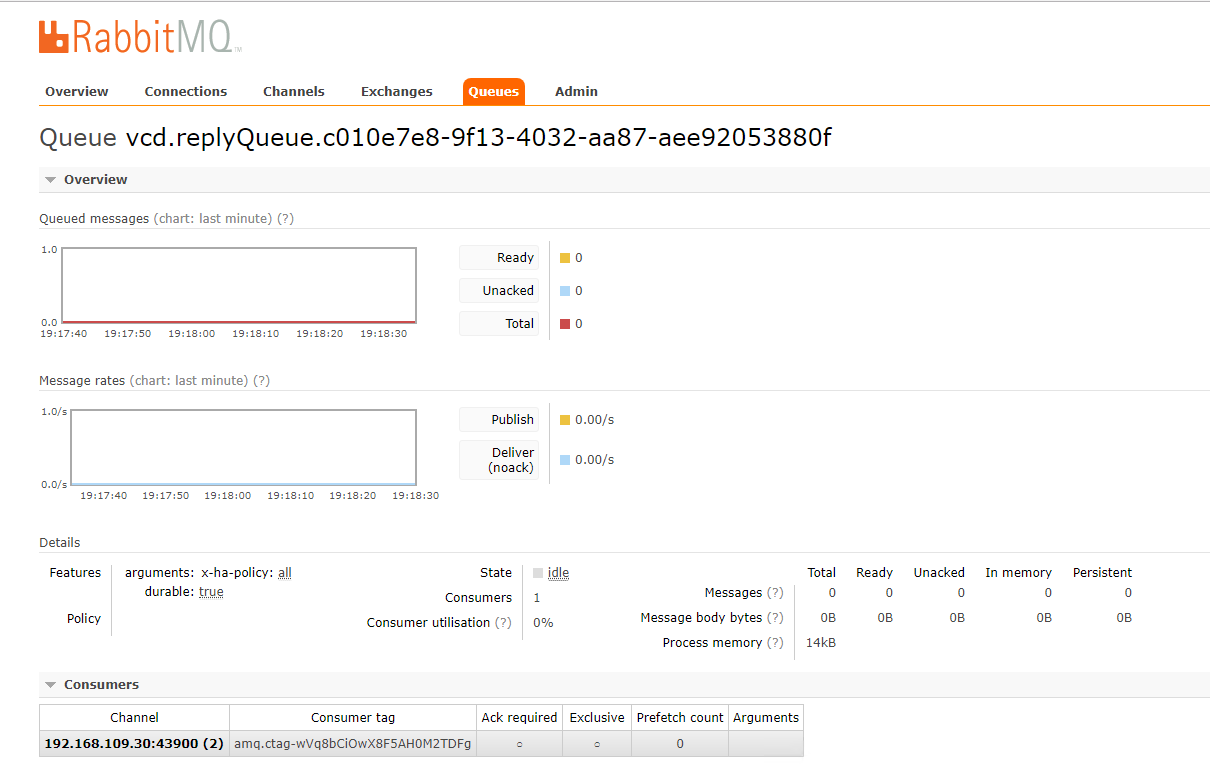
If you login to RMQ, you will see a few queues created and the vCD cell as a consumer.
And that’s it for this post. In the next post of this series, we will deploy the vSphere Replication appliances.
I hope you enjoyed reading this post. Feel free to share this on social media if it’s worth sharing.