The data that travels between clients and ESXi hosts is encrypted to ensure that the transactions are private and authenticated. The SSL is used to create a secure connection between the clients, ESXi hosts, and/or the vCenter Server. SSL uses TCP/IP and allows SSL-enabled ESXi hosts and/or vCenter Server to authenticate with SSL-enabled clients.
When an ESXi host or vCenter Server is installed, the installation includes SSL certificates. These preinstalled, auto generated certificates are not from an official certificate authority (CA), but they can be used to establish an initial connection.
The vCenter Server uses an SSL certificate when adding ESXi hosts and to connect to managed ESXi hosts whose passwords are stored in the vCenter Server database. After an authenticated encrypted connection is established, a smaller session key is encrypted and exchanged using public and private key pairs.
This shared session key is then used to encrypt and decrypt the data between client and server. Shared secret key encryption generally requires very little processing time, which makes it a viable solution for encrypting large amounts of data between a client and a server.
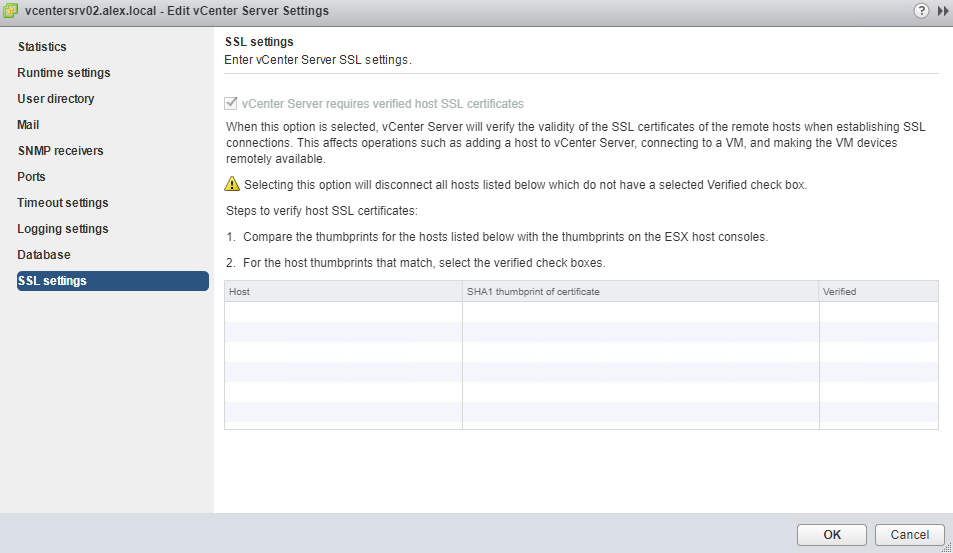
To prevent man-in-the-middle attacks and to fully use the security that certificates provide, certificate checking is enabled by default. You can verify that certificate checking is enabled in the vSphere Web Client by navigating to vCenter Server > Manage > Settings > SSL Settings.

If you click on Edit button, you will find that this option can’t be changed as the option is diminished in Web Client. Also this option is not present in C# client.
I found this topic a bit strange to be frank as there is not much information available on this in vSphere 6 docs.
I hope you find this post informational. Feel free to share this on social media if it is worth sharing. Be sociable 🙂
